Say Hello to the Netgear NeoTV Prime and “PrimePwn”
Posted: January 17th, 2013 | Author: zenofex | Filed under: GTVHacker, Netgear, Root | 1 Comment »
Netgear NeoTV Prime
We first broke news of the Netgear NeoTV Prime back in December, and have since been anxiously awaiting its roll out. Today the day arrived and we received our NeoTV Prime.
The NeoTV Prime uses the same form factor and hardware design as the Vizio Co-Star and Hisense Pulse. The box’s UI is a stock Google TV interface and is identical to some of the other Google TV devices.
The remote however is much different than the rest, with a smaller size and thickness plus a clickable mouse, the remote is much easier to hold and use. Although the remote is well thought out, the D-Pad leaves room for improvement. Furthermore, there does not appear to be a microphone which means the voice search additions coming with version 3 may require an additional purchase.
On to the exploits!
What would be the point of a simple first look post without some exploits!? In fact, this root method may be simpler than the method we previously disclosed for the Hisense Pulse. While the last one required ADB, this method only needs a properly set up USB drive.
Software Method:
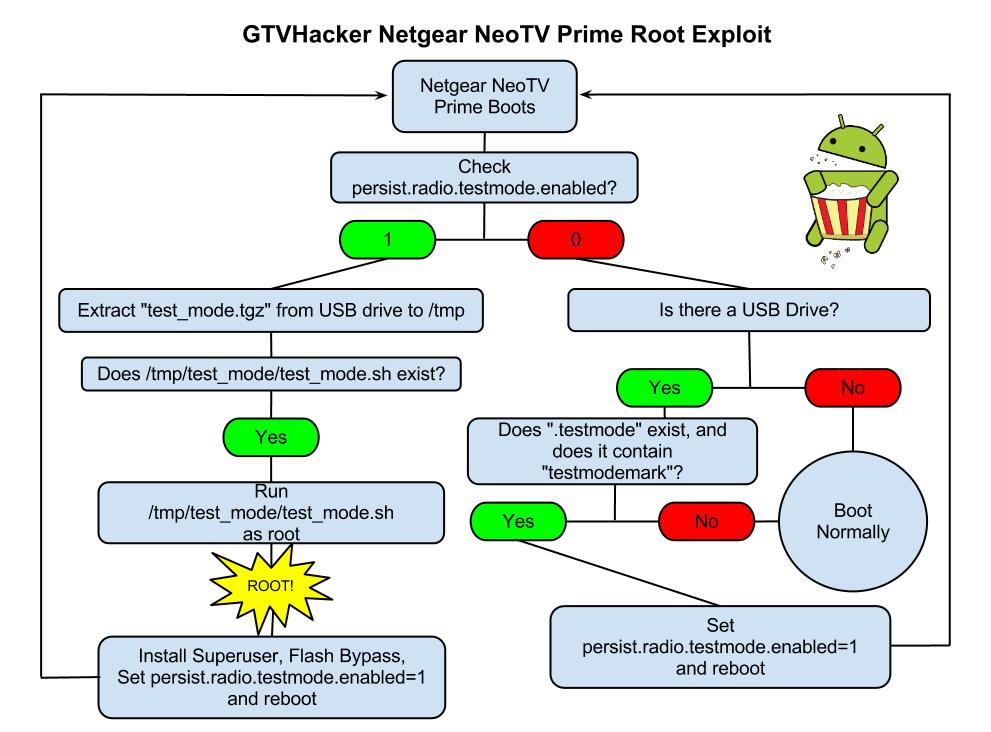
The NeoTV Prime runs a debug service called “testmode” which checks for a USB drive with a file named “.testmode” containing the magic string “testmodemark”. The system then checks to see if the file contains the magic string “testmodemark”. If the system finds the file, it sets the “persist.radio.testmode.enabled” property to 1 and reboots. Then, if the device detects this property as 1 upon boot, it attempts to copy and then extract a file named “test_mode.tgz” from the USB drive to /tmp/. After extracting, the system tries to run a sh file named “/tmp/test_mode/test_mode.sh”. Assuming we set the permissions correctly this file will allow us to run the payload of our choosing as root.
The Following are Automatically Performed:
- Installs SuperSu.apk
- Disables automatic updates
- Modifies flash plug-in to allow streaming of Hulu and other previously blocked content providers
Neo TV “PrimePwn” Root Process:
1.) Download PrimePwn.zip
2.) Extract the PrimePwn.zip to a Fat32 formatted USB drive. (test_mode.tgz, .testmode, README)
3.) Put the USB drive into your NeoTV Prime and reboot.
4.) Let the process run, it will reboot a few times and then will end at the home screen. (Approximately 3 minutes later)
5.) Remove your USB drive.
Extra:
Netgear was kind enough to add an extra line in the init script that forces the hardware (UART) console to spawn as root. The box can be difficult to take apart and the software root is an easy process so we don’t recommend you use this method. We just wanted to mention its existence.
GTVHacker Wiki: Netgear NeoTV Prime
Enjoy!



How do I place the unzipped PrimePwn files to a “root” part of my FAT32 USB storage device?