Posted: January 17th, 2013 | Author: zenofex | Filed under: Uncategorized | Tags: GTVHacker, Netgear, Root | 1 Comment »

Netgear NeoTV Prime
We first broke news of the Netgear NeoTV Prime back in December, and have since been anxiously awaiting its roll out. Today the day arrived and we received our NeoTV Prime.
The NeoTV Prime uses the same form factor and hardware design as the Vizio Co-Star and Hisense Pulse. The box’s UI is a stock Google TV interface and is identical to some of the other Google TV devices.

Netgear NeoTV Prime Remote
The remote however is much different than the rest, with a smaller size and thickness plus a clickable mouse, the remote is much easier to hold and use. Although the remote is well thought out, the D-Pad leaves room for improvement. Furthermore, there does not appear to be a microphone which means the voice search additions coming with version 3 may require an additional purchase.
On to the exploits!
What would be the point of a simple first look post without some exploits!? In fact, this root method may be simpler than the method we previously disclosed for the Hisense Pulse. While the last one required ADB, this method only needs a properly set up USB drive.
Software Method:
The NeoTV Prime runs a debug service called “testmode” which checks for a USB drive with a file named “.testmode” containing the magic string “testmodemark”. The system then checks to see if the file contains the magic string “testmodemark”. If the system finds the file, it sets the “persist.radio.testmode.enabled” property to 1 and reboots. Then, if the device detects this property as 1 upon boot, it attempts to copy and then extract a file named “test_mode.tgz” from the USB drive to /tmp/. After extracting, the system tries to run a sh file named “/tmp/test_mode/test_mode.sh”. Assuming we set the permissions correctly this file will allow us to run the payload of our choosing as root.
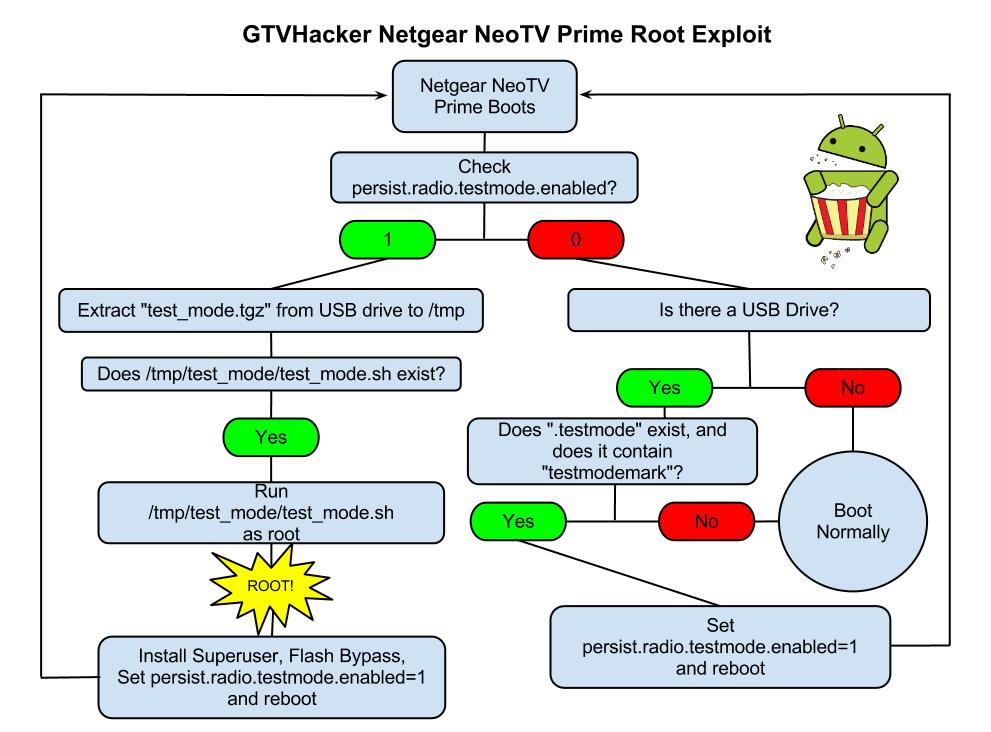
Netgear NeoTV PrimePwn Root Process
The Following are Automatically Performed:
- Installs SuperSu.apk
- Disables automatic updates
- Modifies flash plug-in to allow streaming of Hulu and other previously blocked content providers
Neo TV “PrimePwn” Root Process:
1.) Download PrimePwn.zip
2.) Extract the PrimePwn.zip to a Fat32 formatted USB drive. (test_mode.tgz, .testmode, README)
3.) Put the USB drive into your NeoTV Prime and reboot.
4.) Let the process run, it will reboot a few times and then will end at the home screen. (Approximately 3 minutes later)
5.) Remove your USB drive.
Demo Video

Netgear NeoTV Prime UART Pinout
Extra:
Netgear was kind enough to add an extra line in the init script that forces the hardware (UART) console to spawn as root. The box can be difficult to take apart and the software root is an easy process so we don’t recommend you use this method. We just wanted to mention its existence.
GTVHacker Wiki: Netgear NeoTV Prime
Enjoy!
Purchase at Amazon or Newegg
Discuss More…
Posted: January 3rd, 2013 | Author: cj_000 | Filed under: Uncategorized | Tags: Custom Recovery, Exploit, Generation 2, GTVHacker, Hisense, Recovery, Root, sony, Vizio | Comments Off on GTVHacker – A Brief History And a Sneak Peek
A little over 2 years ago a band of miscreants came together from an XDA developers forum post and started working together to get privileged code execution on the Google TV. Little did we know that the challenges would be greater than anyone could imagine.
 When the Google TV was released it was easily one of the most locked down Android devices containing a signature enforced bootloader which established a “chain of trust” between it and every component loaded thereafter. The hardened state of the kernel the device came with made things even worse, with the kernel enforcing module signing as well as lacking most of the popular Android vulnerabilities that were plaguing the mobile world. This Android device was truly unlike most others.
When the Google TV was released it was easily one of the most locked down Android devices containing a signature enforced bootloader which established a “chain of trust” between it and every component loaded thereafter. The hardened state of the kernel the device came with made things even worse, with the kernel enforcing module signing as well as lacking most of the popular Android vulnerabilities that were plaguing the mobile world. This Android device was truly unlike most others.
So we began work attempting to win an advertised cash bounty for being the first to gain root access on the newly released device. After some work, we posted the first root method for the Logitech Revue, winning a $500 prize. Since then it has been our goal to make Google TV an open platform by unlocking each released device. There were plenty of challenges along the way, in the form of long nights reversing code and many bricked devices. But along with the challenges there have also been many triumphs in the form of releases.
Going over some of our biggest acheivements in the last 2 years:
- Found and released a hardware root method for the Logitech Revue and assisted Dr. Dan Rosenberg in finding a software root exploit.
- Found and released multiple exploits for the Sony NSZ-GT1 and Sony Google TV television line, breaking the established chain of trust.
- Received a secret message from Logitech within the stock recovery on the Logitech Revue.
- Released our own customized and completely open Google TV kernel which utilized a chain of exploits to execute.
- Had the opportunity to present at the 20th annual “DEFCON” security conference in which we we teased a root exploit for the newly released NSZ-GS7 but are still waiting to leverage it until more hardware comes out.
- While working on porting the Boxee OS to the Google TV we found and released 2 exploits which have enabled the Boxee community to install a popular modification package known as Boxee+.
- We released a modification package for the Hisense Pulse which leveraged the intial debug configuration of the device for root, disabled automatic updates, and modified the flash plug-in allowing you to watch Hulu and other previously blocked content providers.
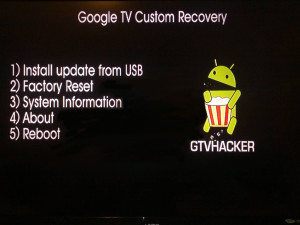 In regards to the future of GTVHacker, over the past month we found and have been developing an exploit which will allow for custom kernels to be run on most of the newest generation of Google TV devices. We’ve also (cj_000 specifically) been busy making a custom recovery specifically designed for the Google TV. You may already know this but, there are a number of differences between the Google TV and other Android devices and these difference make it impossible to simply build a popular AOSP based recovery or kernel image. Due to these differences, we had to make our own recovery from scratch. At the time of writing this it’s still in a beta phase and rather simple. It only allows for installation of an update.zip package from usb. This can be a modified update, a superuser binary and apk or whatever else you wish. We’ve also started adb over ethernet to allow for custom system changes that may require more interaction than a update package.
In regards to the future of GTVHacker, over the past month we found and have been developing an exploit which will allow for custom kernels to be run on most of the newest generation of Google TV devices. We’ve also (cj_000 specifically) been busy making a custom recovery specifically designed for the Google TV. You may already know this but, there are a number of differences between the Google TV and other Android devices and these difference make it impossible to simply build a popular AOSP based recovery or kernel image. Due to these differences, we had to make our own recovery from scratch. At the time of writing this it’s still in a beta phase and rather simple. It only allows for installation of an update.zip package from usb. This can be a modified update, a superuser binary and apk or whatever else you wish. We’ve also started adb over ethernet to allow for custom system changes that may require more interaction than a update package.
Below is a quick demo of the custom recovery mentioned above being tested on a Sony NSZ-GS7 Google TV device. We currently don’t have a release date set as we are trying to keep most of the specifics private in order to avoid an update that could patch the exploit before the community gets to utilize it. We just wanted to give the community a sneak peek at what we’ve been working on privately over the last few months. So sit tight, 2013 will be a great year for the Google TV and GTVHacker!
Discuss More…
Posted: January 1st, 2013 | Author: zenofex | Filed under: Uncategorized | Tags: Hisense | Comments Off on Hisense Pulse – The Verdict is Accident
 If you remember our previous post about the Hisense Pulse and its original shipping configuration then you’ll remember that the device, unlike all others in the Google TV line, came almost completely unlocked. Specifically, it shipped with a hardware root shell in recovery and normal boot modes, as well as allowed adb to be rebooted as root with a simple command. At the time we were wondering based on how open this device was shipped, was this an accident or was this a show of support to the “customizing” Google TV community? Well the verdict is in after an update was released this morning patching all current Hisense Pulse root methods. In particular, the update that was released today (BOX_2.31a.C1204_E_release , download here ) changes the “ro.debugabble” prop to 0 causing the hardware root method as well as the “adb root” command to no longer work. At the moment there is no other public root method but don’t worry, if you haven’t updated yet you can still run our “Pulse Modification Package” from the Hisense Pulse section of the wiki which disables automatic updates. Also, if you haven’t purchased a Pulse yet or have one already on the way, the Pulse will continue to ship “unlocked” for the time being. If we use the Logitech Revue as a reference point, since it shipped with hardware root shell in recovery mode until it was discontinued, newly purchased Pulse units may never be patched but will need to be rooted before their initial setup.
If you remember our previous post about the Hisense Pulse and its original shipping configuration then you’ll remember that the device, unlike all others in the Google TV line, came almost completely unlocked. Specifically, it shipped with a hardware root shell in recovery and normal boot modes, as well as allowed adb to be rebooted as root with a simple command. At the time we were wondering based on how open this device was shipped, was this an accident or was this a show of support to the “customizing” Google TV community? Well the verdict is in after an update was released this morning patching all current Hisense Pulse root methods. In particular, the update that was released today (BOX_2.31a.C1204_E_release , download here ) changes the “ro.debugabble” prop to 0 causing the hardware root method as well as the “adb root” command to no longer work. At the moment there is no other public root method but don’t worry, if you haven’t updated yet you can still run our “Pulse Modification Package” from the Hisense Pulse section of the wiki which disables automatic updates. Also, if you haven’t purchased a Pulse yet or have one already on the way, the Pulse will continue to ship “unlocked” for the time being. If we use the Logitech Revue as a reference point, since it shipped with hardware root shell in recovery mode until it was discontinued, newly purchased Pulse units may never be patched but will need to be rooted before their initial setup.
It’s sad to find out that the little bit of hope we had about this being a show of community support, as opposed to an accident, is now gone. We will continue to help the community “free” their devices as we have on the rest of the Google TV platform while hoping for the much needed release of a true Google TV “Nexus” device.
Discuss More…







