Hisense Pulse: Insecure at launch, accident or a message?
Posted: December 22nd, 2012 | Author: zenofex | Filed under: GTVHacker, Hisense, Root | Tags: google, Hisense, Pulse, Root, TV | 2 Comments » The day has finally arrived, the Hisense Pulse has launched and is finally in our hands. Upon first look we were impressed with the speed of navigation from within the menus. If you have experience with the previous generation of the Google TV platform then you’ll recognize the Pulse’s UI which seems to be almost identical to that of the Logitech Revue. The form factor of the Pulse is similar in size and shape to that of the already released Vizio Co-Star, and the motherboard layout makes it seem like they used a similar design. One difference between the Co-Star and the Pulse is that the Pulse’s remote is much more intuitive and its use feels more natural. All together it’s exactly what someone would expect for another device in the Google TV family but with one of the cheapest prices in its generation.
The day has finally arrived, the Hisense Pulse has launched and is finally in our hands. Upon first look we were impressed with the speed of navigation from within the menus. If you have experience with the previous generation of the Google TV platform then you’ll recognize the Pulse’s UI which seems to be almost identical to that of the Logitech Revue. The form factor of the Pulse is similar in size and shape to that of the already released Vizio Co-Star, and the motherboard layout makes it seem like they used a similar design. One difference between the Co-Star and the Pulse is that the Pulse’s remote is much more intuitive and its use feels more natural. All together it’s exactly what someone would expect for another device in the Google TV family but with one of the cheapest prices in its generation.
Our biggest and most unexpected surprise came within moments of our first examination of the Pulse. Upon receiving any new hardware, partially because of our previous experience with the Revue, we like to start off disassembling the hardware even before powering on a device. After doing so in this particular instance we found that a hardware root-shell is enabled by default through the serial console header on the device’s motherboard. Better yet, the root-shell is available in both recovery and normal boot which allows for tinkering of the device in both modes of operation.  While we’ve seen serial consoles left in prior Google TV devices (see: Logitech Revue), we had yet to see a Google TV device that included a shell within both normal and recovery mode, let alone one in the second generation of the Google TV platform. While leaving a hardware shell leaves the box almost completely vulnerable its use still requires some soldering experience. However, after further exploration we noticed a 4 pin header on the Pulse PCB which allowed us to simply plug in a common connector and avoid soldering all together! This adapter is conveniently in a location that can be accessed by either temporarily opening the device and plugging in the adapter, or for more permanent use, by cutting a hole in the side of the case. The ease of access to the pin header as well as the obvious oversight of the serial console was just the beginning of our findings.
While we’ve seen serial consoles left in prior Google TV devices (see: Logitech Revue), we had yet to see a Google TV device that included a shell within both normal and recovery mode, let alone one in the second generation of the Google TV platform. While leaving a hardware shell leaves the box almost completely vulnerable its use still requires some soldering experience. However, after further exploration we noticed a 4 pin header on the Pulse PCB which allowed us to simply plug in a common connector and avoid soldering all together! This adapter is conveniently in a location that can be accessed by either temporarily opening the device and plugging in the adapter, or for more permanent use, by cutting a hole in the side of the case. The ease of access to the pin header as well as the obvious oversight of the serial console was just the beginning of our findings.
After finishing up our quick analysis of the hardware we finally had the opportunity to explore how the device’s software side was configured. We found that even with the hardware root oversight being as unexpected and less secure than any of its counter parts, the software side was worse. After browsing through the system’s init scripts, and checking the props, we noticed that a simple “adb root” to the device would restart adb as root therefore providing us with a root shell via adb.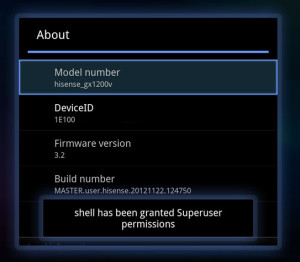
Why is this device so much less secure than any of the other Google TV devices? Is this an oversight, or did someone at Hisense purposely leave it there to show community support? We hope that someone did this purposely as it would be great if a manufacturer or Google finally embraced the modding community, but it was probably just an oversight.
Knowing this, we thought it would be best to release our findings for the community as soon as possible as it will likely be patched quickly with the next automatic update. However, if you do have a Hisense Pulse and would like to take advantage of root before it’s possibly patched. We have a package that will perform a few community desired modifications such as:
- Install Superuser.apk and su binary to device.
- Patch flash player to allow content to be played from previously blocked websites (Hulu, Fox, CBS, NBC, etc.).
- Disable automatic updates to preserve root (can easily be reversed).
You can find information on our modification package at the GTVHacker Wiki page for the Hisense Pulse
We have more coming soon, check back around the first of the year for a sneak peek at something even more awesome than this!
Looking to purchase a Hisense Pulse and also want to support GTVHacker? [Use this link to purchase at Amazon]
Discuss More…